ESDS cybersecurity team handle diverse threats with threat detection. Using advanced tools, we ensure faster incident response with advanced analysis. Backed by 19 years of expertise, our solutions secure data in Indian data centers. Our SOC services offer a pay-as-you-go model for cost efficiency.
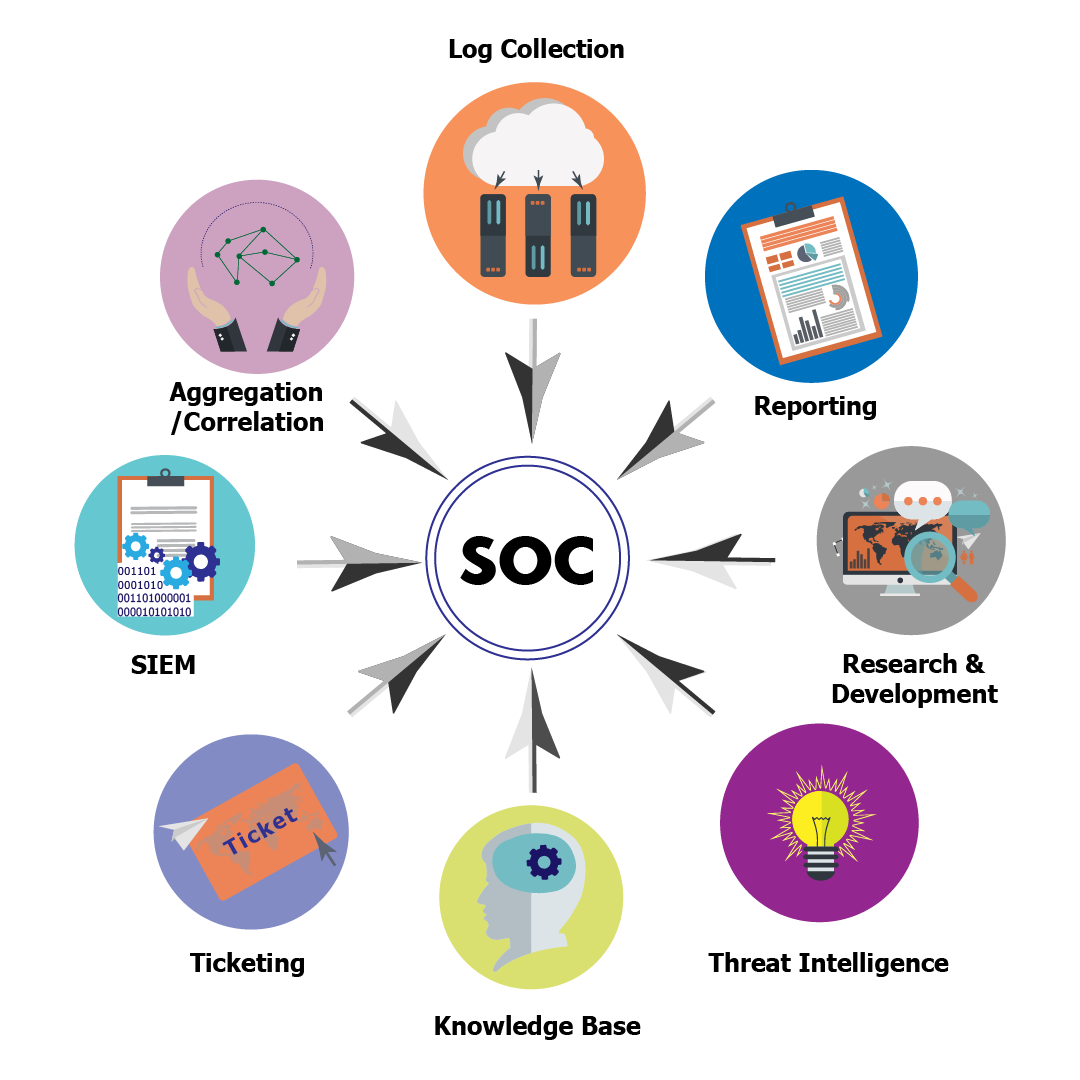
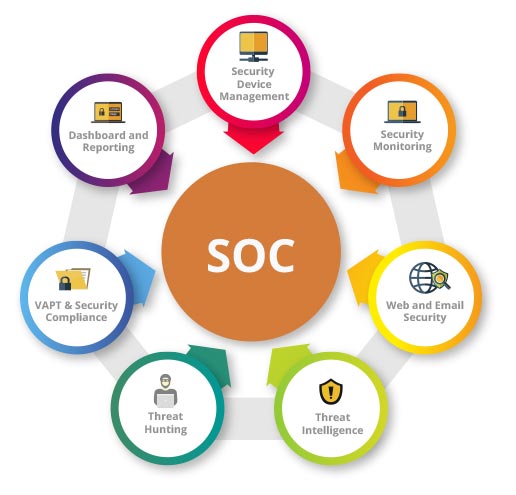
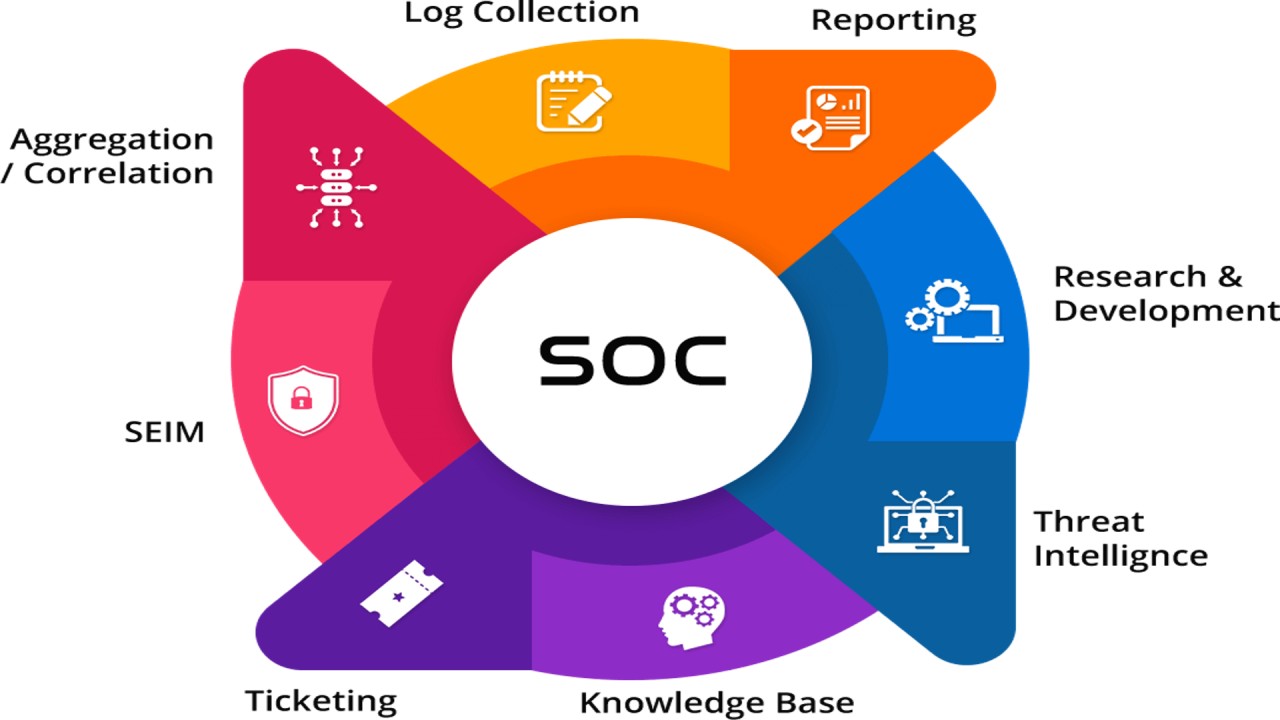
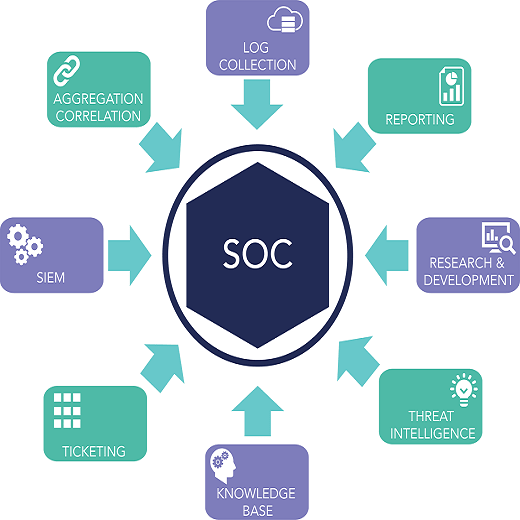
Asset Inventory and Monitoring: Gaining complete visibility into all IT assets (endpoints, servers, databases, cloud resources, etc.) and security tools used to protect them.
Threat Intelligence and Proactive Security: Staying updated on the latest threats, vulnerabilities, and attacker tactics through various intelligence sources (e.g., global intelligence networks, dark web monitoring), and proactively identifying and addressing security gaps before they are exploited.
Continuous Monitoring and Threat Detection: Utilizing tools like SIEM (Security Information and Event Management) and XDR (Extended Detection and Response) to collect and analyze security event data, logs, and network traffic for suspicious activity and potential attacks.
Incident Response and Management: Developing and implementing an incident response plan to handle confirmed security incidents effectively, which includes containing the threat, mitigating damage, eradicating the threat, and recovering compromised systems and data.
Vulnerability Management: Regularly conducting vulnerability assessments and penetration testing to identify and remediate security weaknesses in the organization’s infrastructure and applications.
Log Management: Collecting, analyzing, and maintaining log data generated by all network events to establish baselines, detect anomalies, and aid in investigations.
Compliance Management: Ensuring adherence to relevant security standards and regulatory requirements such as GDPR, HIPAA, PCI DSS, and ISO 27001.
Reporting and Communication: Providing clear and concise reports on security status, incidents, and remediation efforts to stakeholders.
Why are SOC services important?
Minimizing downtime and business disruption: Faster detection and response to threats significantly reduce the impact of cyberattacks on business operations.
Protecting valuable assets: Safeguarding intellectual property, customer data, and other critical assets from theft and compromise.
SOC services
₹399.00 Original price was: ₹399.00.₹299.00Current price is: ₹299.00.
SOC services:
Security Operations Center (SOC) services are a critical component of modern cybersecurity, providing a centralized and coordinated approach to defending an organization’s IT infrastructure and data from the ever-evolving threat landscape.
Stock Available
Related Products
Related products
-
Sale!
Premium Office Setup Package
₹95,000.00Original price was: ₹95,000.00.₹85,000.00Current price is: ₹85,000.00. -
Sale!
Educational websites
₹12,500.00Original price was: ₹12,500.00.₹10,500.00Current price is: ₹10,500.00. -
Sale!
Premium Security Package
₹799.00Original price was: ₹799.00.₹599.00Current price is: ₹599.00. -
Sale!
Advanced Security Package
₹599.00Original price was: ₹599.00.₹399.00Current price is: ₹399.00. -
Sale!
Managed Security Services
₹499.00Original price was: ₹499.00.₹299.00Current price is: ₹299.00.
FAQ
What is digital marketing?
Digital marketing is a multifaceted approach to promoting brands, products, or services using internet-based platforms and technologies. It encompasses a wide variety of channels including search engines, social media, websites, email, mobile applications, and online advertising networks. Its primary objective is to connect with consumers where they spend the majority of their time—online. This method of marketing allows businesses to target specific audiences based on their interests, behaviors, demographics, and online activities. It includes strategies such as Search Engine Optimization (SEO) to increase organic traffic, Pay-Per-Click (PPC) advertising for paid visibility, email campaigns for direct communication, content marketing to provide value and build authority, and social media marketing for community engagement and brand visibility. Unlike traditional marketing, which often relies on one-way communication through TV, radio, or print media, digital marketing is interactive, data-driven, and measurable. This means marketers can analyze the success of their campaigns in real time, make adjustments quickly, and optimize performance for better results. With the right strategy, digital marketing can generate leads, drive sales, enhance customer loyalty, and deliver a significant return on investment.
Why is digital marketing important today?
How is digital marketing different from traditional marketing?
Can digital marketing work for any business?
How can smaller companies stand out against bigger firms in digital marketing?
Why Every Business Needs A Website
What is a website and why is it important to have?
A website is a collection of web pages under a single domain (e.g., www.yourcompany.com) that digitally represent a business, organization, or individual. At its core, a website is a tool for communication and connection that can be accessed anytime, from anywhere, via a web browser.
15 benefits of a website for business growth.
Boosting SEO performance leading to more organic traffic.
Customer Reviews
Social Media Posts
This is a gallery to showcase images from your recent social posts

tapas nath –
very good product for computer software.